
How to Replace Your Firewall (Firewall Migration Plan) (2022)
3. Pick the Vendor and Hardware - Enterprise-Level vs. Mainstream. There are many firewall vendors and products in the marketplace, each with their own strengths and weaknesses. Examine your sizing, business requirements, network complexity, and other factors to determine which firewall is right for your organization.

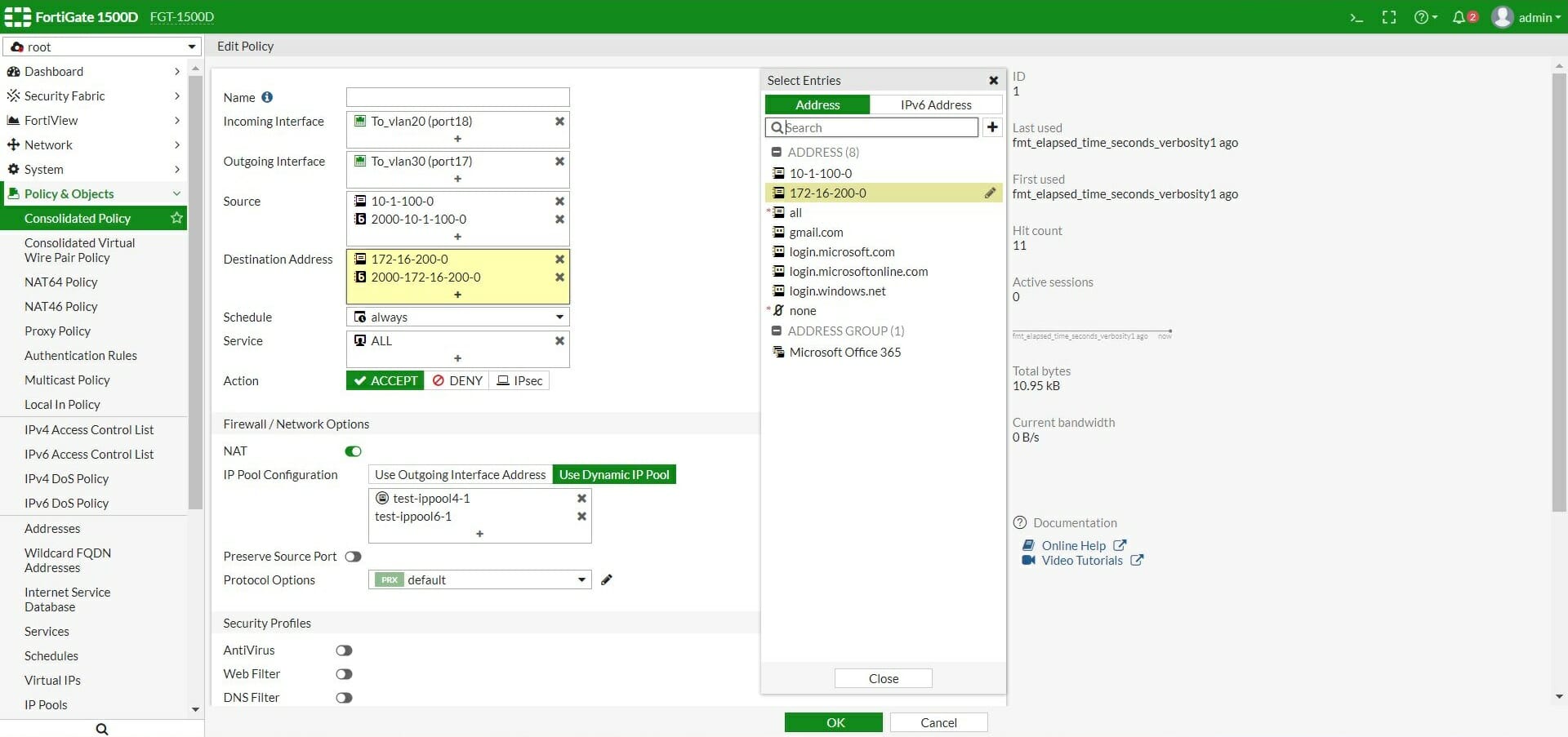
Implementation of Firewall Policies FortiGate (Part 2) Hacking Articles
Firewall Implementation & Maintenance Practices Best Practice Checklist Understanding the basics: A layperson's guide and checklist for overseeing IT. An exclusive publication of Sandbox Technologies, Inc. 4111 West Alameda Avenue, Suite 605 Burbank, CA 91505 Tel. (424) 207-5130 www.sandboxtech.com

Project Deployment Plan PowerPoint Template PPT Templates
Outcomes of the firewall implementation planning phase will determine how to best configure and deploy firewalls into production. Firewall Configuration. The next phase of firewall design and implementation is configuring firewalls and integrating them into your organization's security architecture. The NIST recommends several processes for.
Implementation of Firewall Policies FortiGate (Part 1)
Here's how ClickUp's Firewall Implementation Project Plan Template can help your IT department: Streamline the entire implementation process, from initial setup to final testing. Assign tasks and deadlines to team members for efficient collaboration. Monitor progress and track milestones to keep the project on schedule.
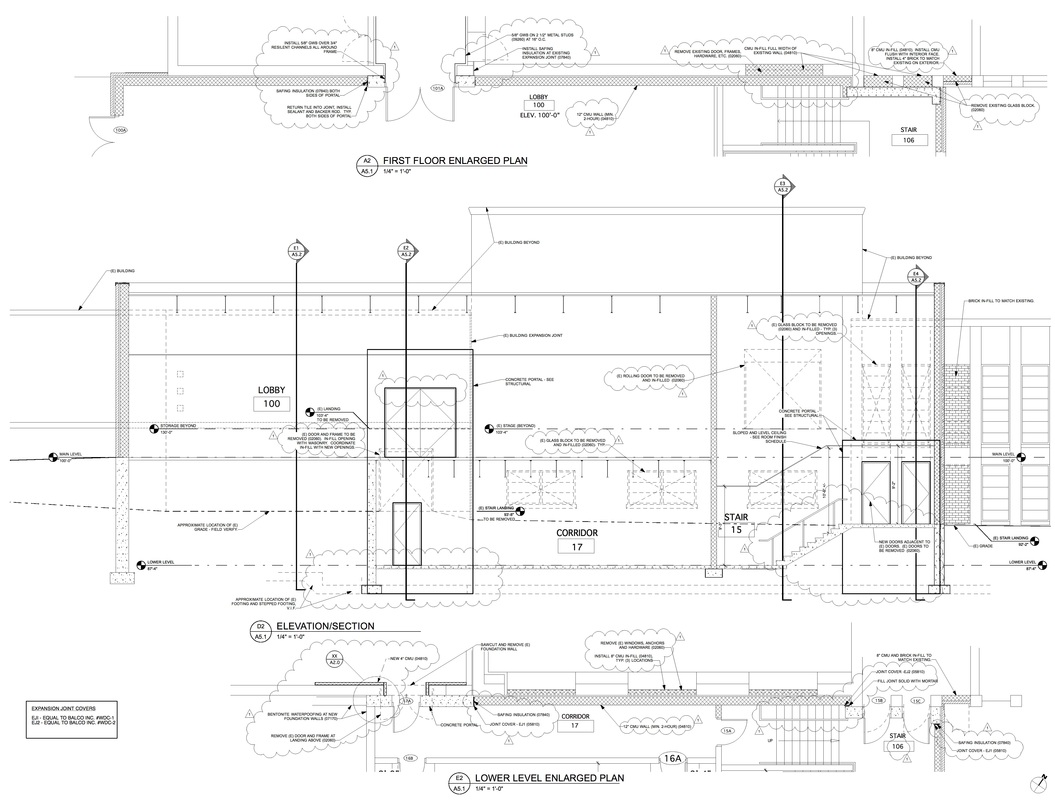
Wiki Blog Architekwiki
Our project approach. Below you can see an example of a 7-step approach to a firewall migration plan. The plan applies, whether it is an external firewall providing perimeter security or an internal firewall solution defending your internal network segments. 1 - Understand. The first step in a project such as this is to understand your business.
Free 10 Migration Project Plan Examples Pdf Examples Cloud Migration
A7.3 Iterative procedure for implementation - from basic security to full protection 20 7.3.1 Step 1: Specification of role distribution / inclusion of application development 20 7.3.2 Step 2: Basic protection for all web applications 20 7.3.3 Step 3: Creating a priority list of all existing web applications 20
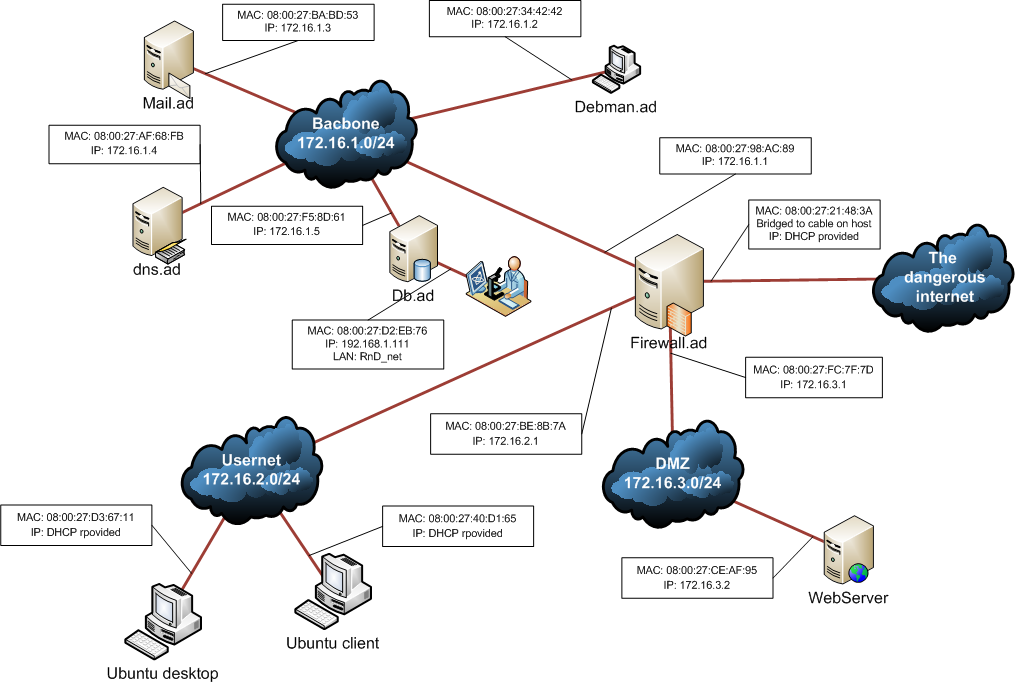
Final Demo Plan Firewall Project
Planning and design come together in mapping business solutions that actually address objective needs. These phases look at different angles to see if actual issues have been addressed, taking into account cost, timing, and ROI evaluation. Design and implementation include final review of design and timelines, beginning stages of project
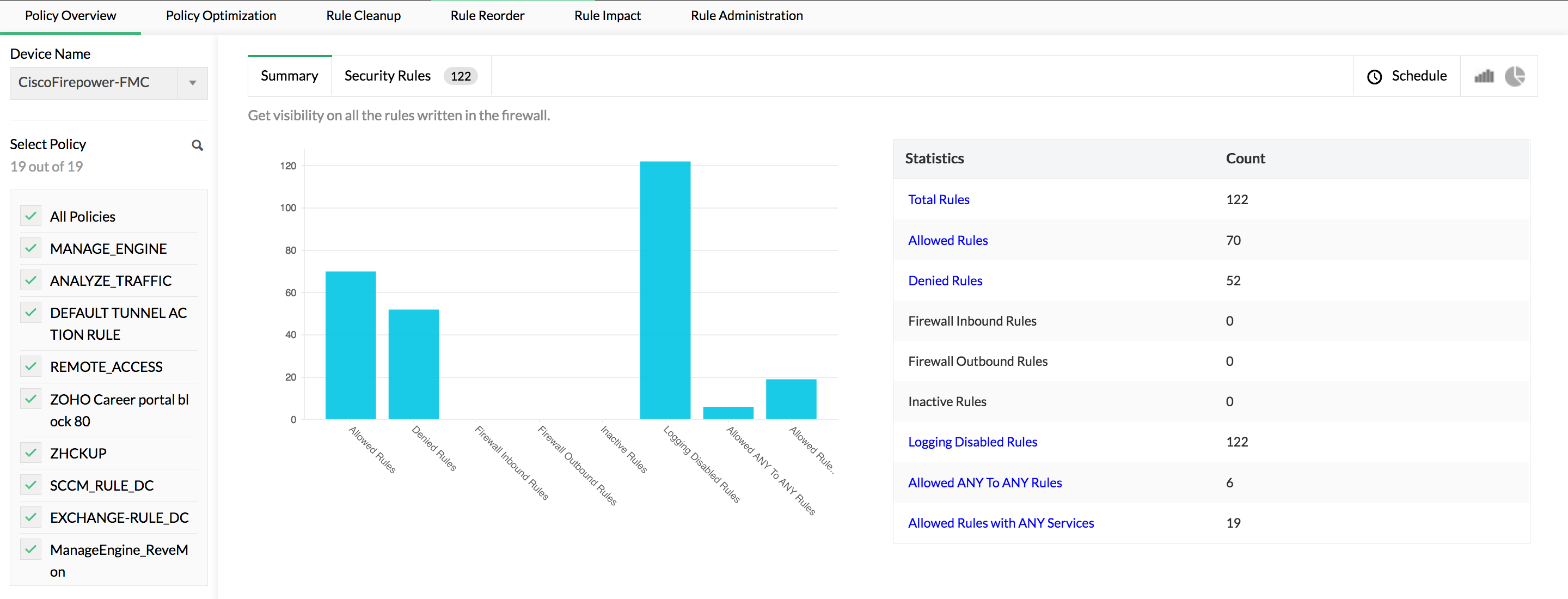
Firewall Management Software Firewall Management Tools ManageEngine
There are many considerations that organizations should include in their firewall selection and planning processes. Organizations need to determine which network areas need to be protected, and which types of firewall technologies will be most effective for the types of traffic that require protection. Several
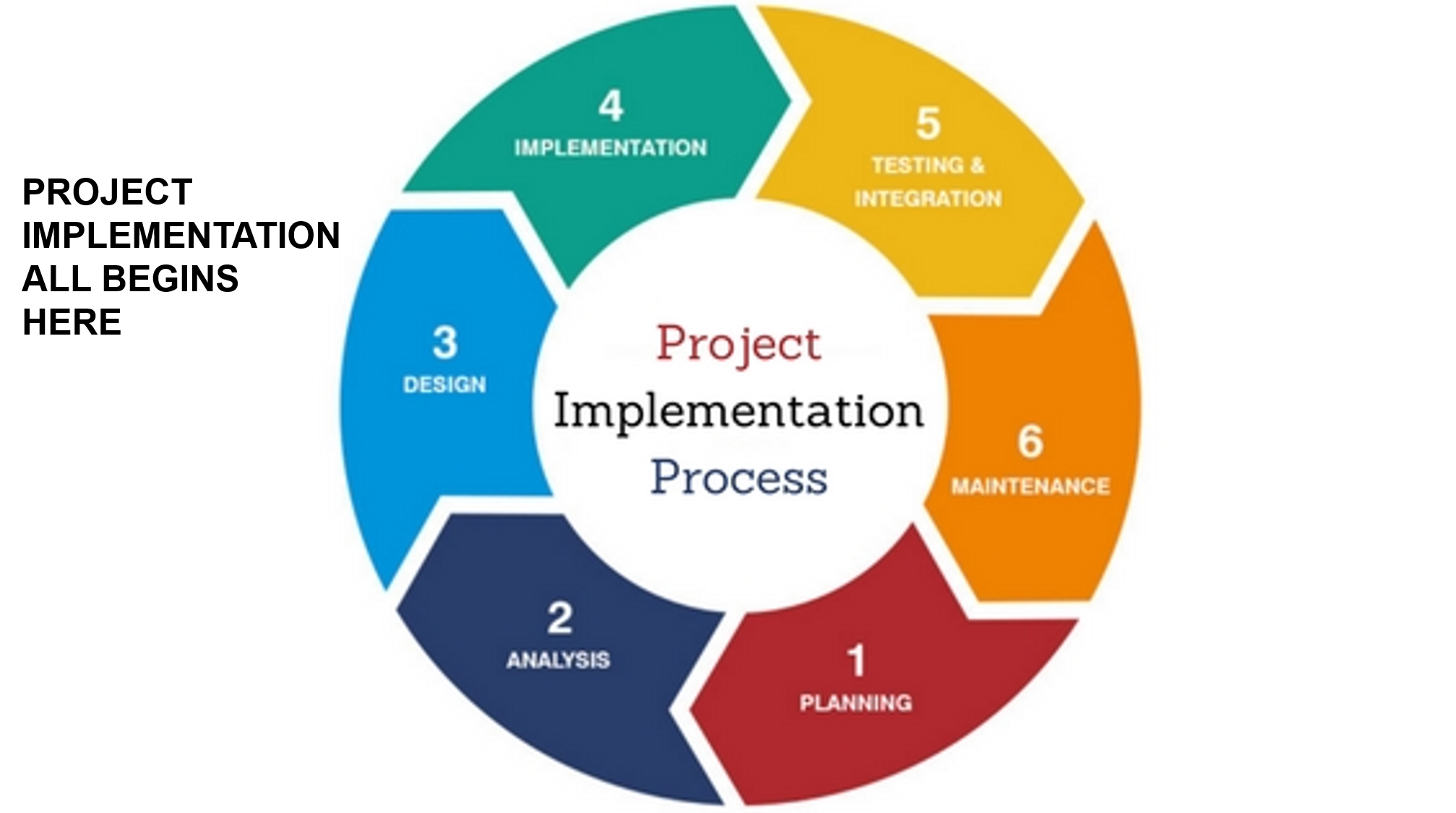
Project Implementation, Control, and Closure StudiousGuy
The Country-wide Established of Standards and Technology (NIST) recommends a five-stage approach that enterprises can apply for robust firewall design and implementation: Planning firewall design and implementation to meet securing needs; Configuring firewalls in shift with an firewall policy; Testing firewalls up optimize layouts

Firewall Management Essentials Change Management 推酷
WaTech plans to manage the NextGen Firewall Implementation project in two phases. During Phase 1, from Feb. 2023 to Sept. 2024, WaTech will: Refresh core and edge firewall hardware and migrate all existing production traffic to the new hardware. Consolidate equipment and migrate existing edge Intrusion Prevention (IPS) functionality to the new.

jerarquía manual Empresa router firewall level laberinto Ataque de
3. Installation, Configuration, and Maintenance of the Firewalls. Once a vendor has been chosen, the final step in setting up your firewall is the actual implementation. The IT provider you have chosen will install the solution in your environment, covering all of the areas you deemed necessary in your earlier assessment.
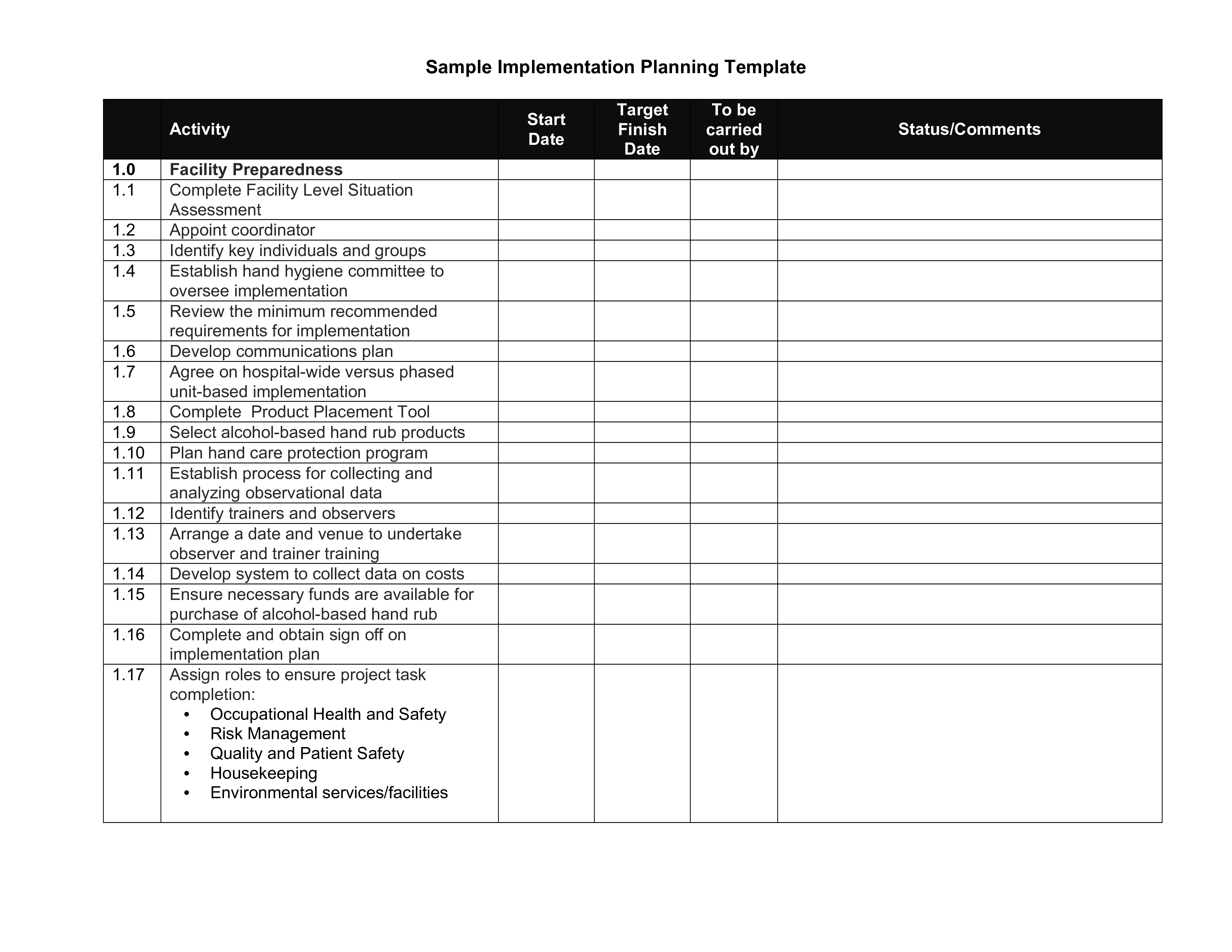
Sample Implementation Plan Gratis
Configure a best-practice security policy rulebase to safely enable applications and protect your network from attack. Go to the Best Practices page and select security policy best practice for your firewall deployment. Set up High Availability —High availability (HA) is a configuration in which two firewalls are placed in a group and their.

Firewall Implementation Neelatech
Firewall is a system designed to prevent unauthorized access to or from a private network. They can be implemented in both hardware and software, or a combination of both.. In our implementation, we have used the struct ip structure as an header to the payload that is sent. ip is a struct (structure) in the C programming language..
Firewall Migration & Replacement Project Manx Technology Group
implementation of your Palo Alto Networks firewall to maximize its effectiveness. Our certified team of experts will help you navigate the daunting task of firewall policy and configuration, and support the smooth migration of your existing firewall configurations. Our real-world experience designing, implementing, and operating
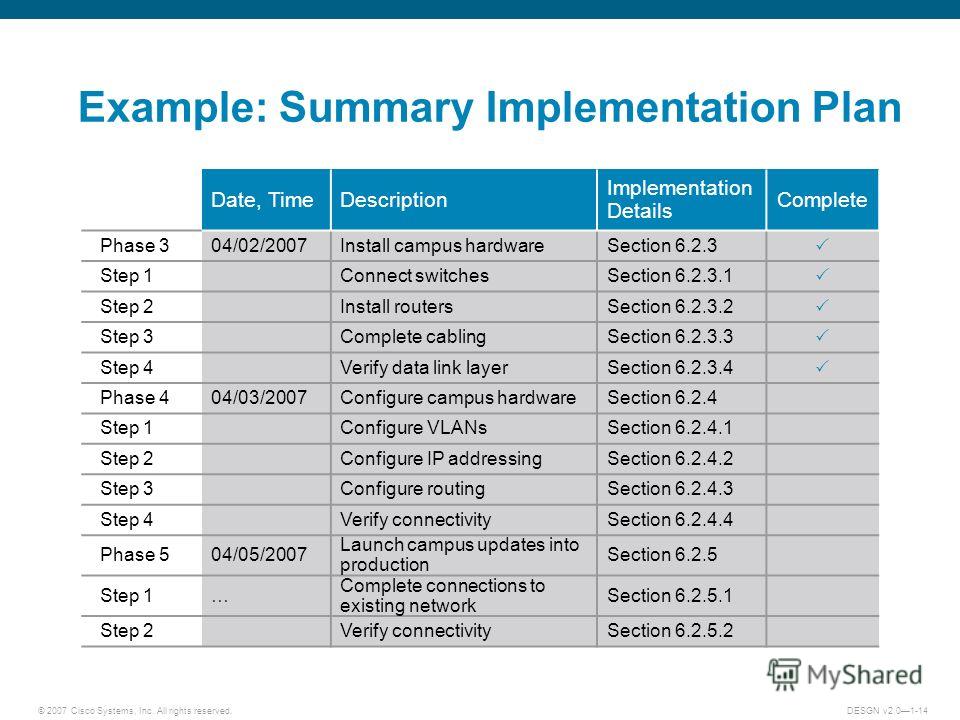
It Network Implementation Plan Template Peatix
Here are some excellent and must-follow best practices to make the most of your firewall program: 1. Ensure minimum access rights. When installing a firewall, configure all the access rules and controls for both outbound and inbound communication. Only offer access in a granular, as-needed form - only when it is necessary for business operations.

Firewall Adalah Pengertian, Fungsi, Jenis, Cara Kerja dan
For the first goal, it provides the firewall definition, discusses the functions, possible architectures, and operational models concentrating on the presentation of their advantages and drawbacks. It includes the step‐by‐step guide to the firewall design and implementation process ranging from planning to deployment and maintenance.