
LoadBalancingdesTrendMicroInterScanWebSecurityWebGatewayWebf…
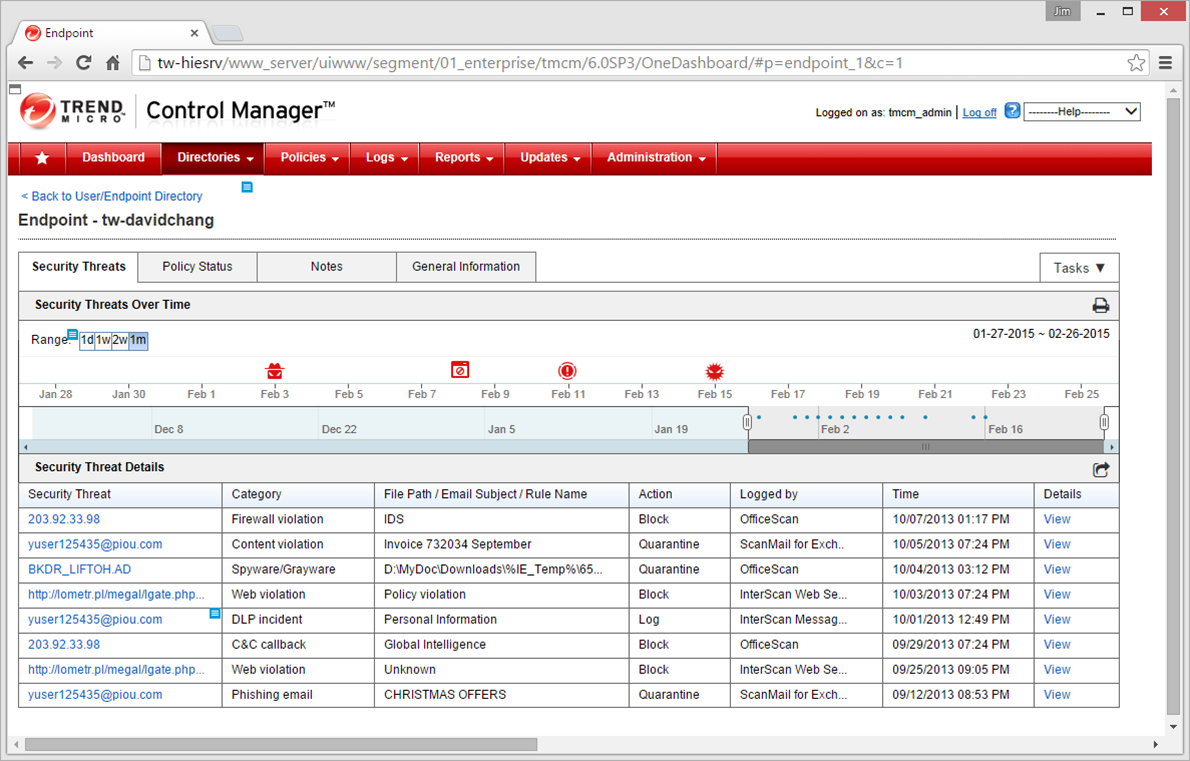
trend-micro-remote-manager-interscan-web-securi_005 Print. Trend Micro Web Security Events. Views: Table 1. Threat Events Event Category Details Event Status Antispyware Spyware/Grayware detections : The detected spyware/grayware count during the last 24 hours.

Trend Micro InterScan Messaging Security Virtual Appliance
© Trend Micro Incorporated. All rights reserved. An on-premises secure web gateway that gives you superior protection against dynamic online threats, while providing you with real-time visibility and control of employee internet usage.

kreyda Trend Micro Enterprise Security Suite solutions in ITinftrastructure
Event 672 is repeatedly logged in the Domain Controller Security Event Log of InterScan Web security Virtual Appliance (IWSVA) 5.6 Product/Version includes:Interscan Web Security Virtual Appliance , Interscan Web Security Virtual Appliance 5.6, View More Update Date: 2016/11/24 Article Number: 000206542 Category: Configure, Troubleshoot Rating: 0
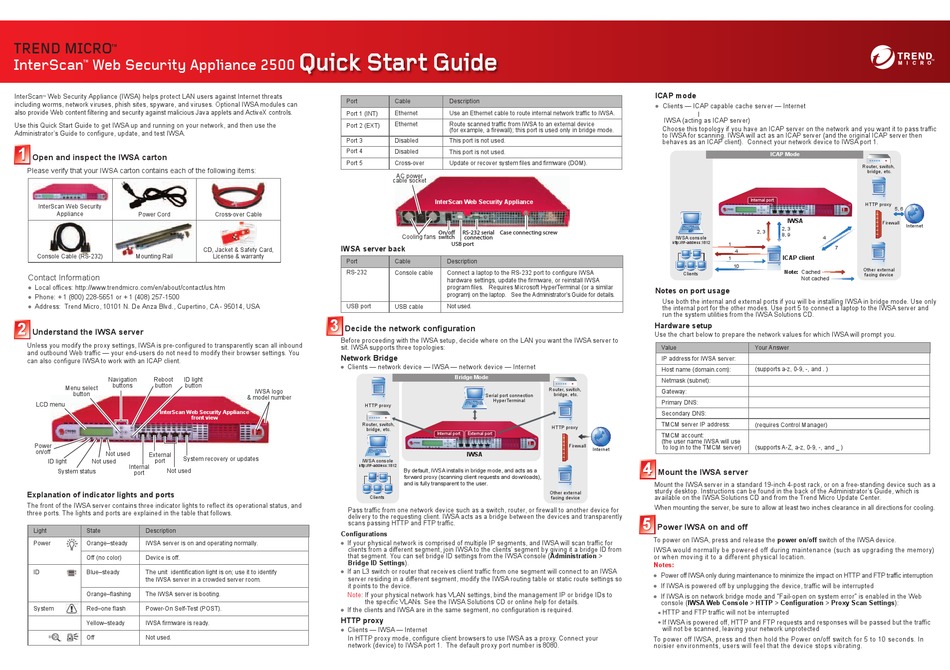
TREND MICRO INTERSCAN WEB SECURITY APPLIANCE 2500 QUICK START MANUAL Pdf Download ManualsLib
Implementing an HTTP Inspection policy in InterScan Web Security Virtual Appliance (IWSVA) can be used to address this scenario.. EVENT: {OP: HEADER_REMOVE HEADER: X-GoogApps-Allowed-Domains} EVENT:. Join our community to discuss the latest topics about Trend Micro products. Service Status.

Trend Micro InterScan Gateway Security Appliance 1.5
The default headline is Trend Micro InterScan Web Security Event (%h). The headline is common for virus infection messages, file type blocking, and URL blocking messages. Note: The URL %U, $$DETAILS and %c tokens can only be used in the main body. %H token only displays below the message.

Getting Started Guide for InterScan Web Security as a Service Manualzz
Tenable found multiple vulnerabilities in Trend Micro InterScan Web Security Virtual Appliance (IWSVA) 6.5 Service Pack 2, build 1901. CVE-2020-28578: Unauthenticated Remote Stack Buffer Overflow The flaw exists in the Java_com_trend_iwss_gui_IWSSJNI_DecryptPasswd function in libuiauutil.so due to improper validation of user-supplied data before copying it to a fixed-size, stack-based buffer.

IT Center Blog Trend Micro Interscan Web Security Appliance 6.5 Security Gateway
Category: Configure Rating: 0 You are viewing an archived article because the product (s) tagged is no longer supported or the information mentioned is already outdated. Summary Allowing or denying URL access via IWSS product can be configured and modified using the management console.
Trend Micro InterScan Messaging Security Suite Multiple Vulnerabilities
trend-micro-remote-manager-managing-interscan-w Print.. Table 1. Trend Micro Web Security Management Tasks Task Description. View a list of Trend Micro Web Security events. Access the Trend Micro Web Security console Access the Trend Micro Web Security console by clicking Open Console .

Trend Micro addresses remote takeover threat in InterScan Web Security Virtual Appliance The
Knowledge Base at Trend Micro's Web site. Trend Micro is always seeking to improve its documentation. If you have questions, comments, or suggestions about this or any Trend Micro documents, please contact us at [email protected]. Your feedback is always welcome. Please evaluate this documentation on the following site:

Trend Micro InterScan Web Security Virtual Appliance IAM Networks
Trend Micro Remote Manager Online Help. Home; Online Help Center; trend-micro-remote-manager-interscan-web-securi_008 Print. Trend Micro Web Security Notifications. Views: System Events Event Details Account sync issues - Sync issues with AD/LDAP : Unable to sync with AD/LDAP

PPT Trend Micro InterScan Web Security Suite ™ 2.5 PowerPoint Presentation ID5173590
Trend Micro InterScan Web Security as a Service dynamically protects against cyber threats in the cloud, before they reach your users or network. It also delivers real-time visibility and control of employee Internet usage.
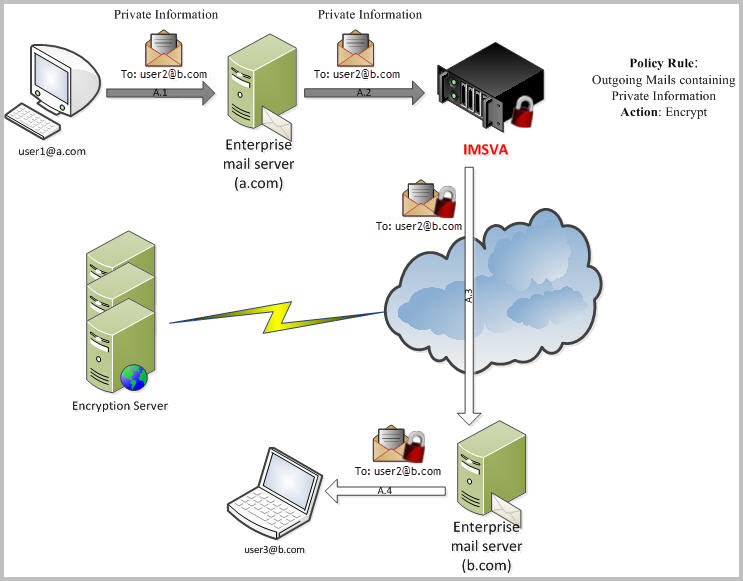
Understanding Email Encryption
Article Number: 000200057 Category: Configure, Deploy, Upgrade Rating: 0 Summary This article lists the most Frequently Asked Questions (FAQs) about IWSaaS. Here are common questions about IWSaaS: Does IWSaaS scan FTP over HTTP? How are log files named? How can I submit suspicious URLs to Trend Micro? How do I determine policy precedence?

Trend Micro™ InterScan™ Web Security Virtual Appliance
available in the online help file and online Knowledge Base at Trend Micro's Web site. Trend Micro is always seeking to improve its documentation. If you have questions, comments, or suggestions about this or any Trend Micro documents, please contact us at [email protected]. Your feedback is always welcome.

Trend Micro InterScan Gateway Security Appliance 1.5
Web Security Protect from internet threats and gain control over cloud app usage Try advanced Try standard Superior protection with centralized management Monitor web use and manage policies with a single management console. Stop threats before they reach endpoints and mobile devices. Protect users at any location, on or off the corporate network.

Trend Micro InterScan Messaging Security Download Scientific Diagram
Trend Micro Web Security Simple. Quick. Cost-effective Solution. Our Cloud Solution Will Help You: How Trend Micro Web Security Works HTTP Click the blue question mark button on any page to open help for that page. Page-level help appears in a panel.

IT Center Blog Trend Micro Interscan Web Security Appliance 6.5 Security Gateway
Online Help Center Print InterScan Web Security Suite Policy Settings Views: This section discusses how to configure InterScan Web Security Suite policy settings in Apex Central. Topics include: Data Loss Prevention Rule List Parent topic: InterScan Security Policies Online Help Center © Trend Micro Incorporated. All rights reserved.